Ultimo aggiornamento:
Root Certificates
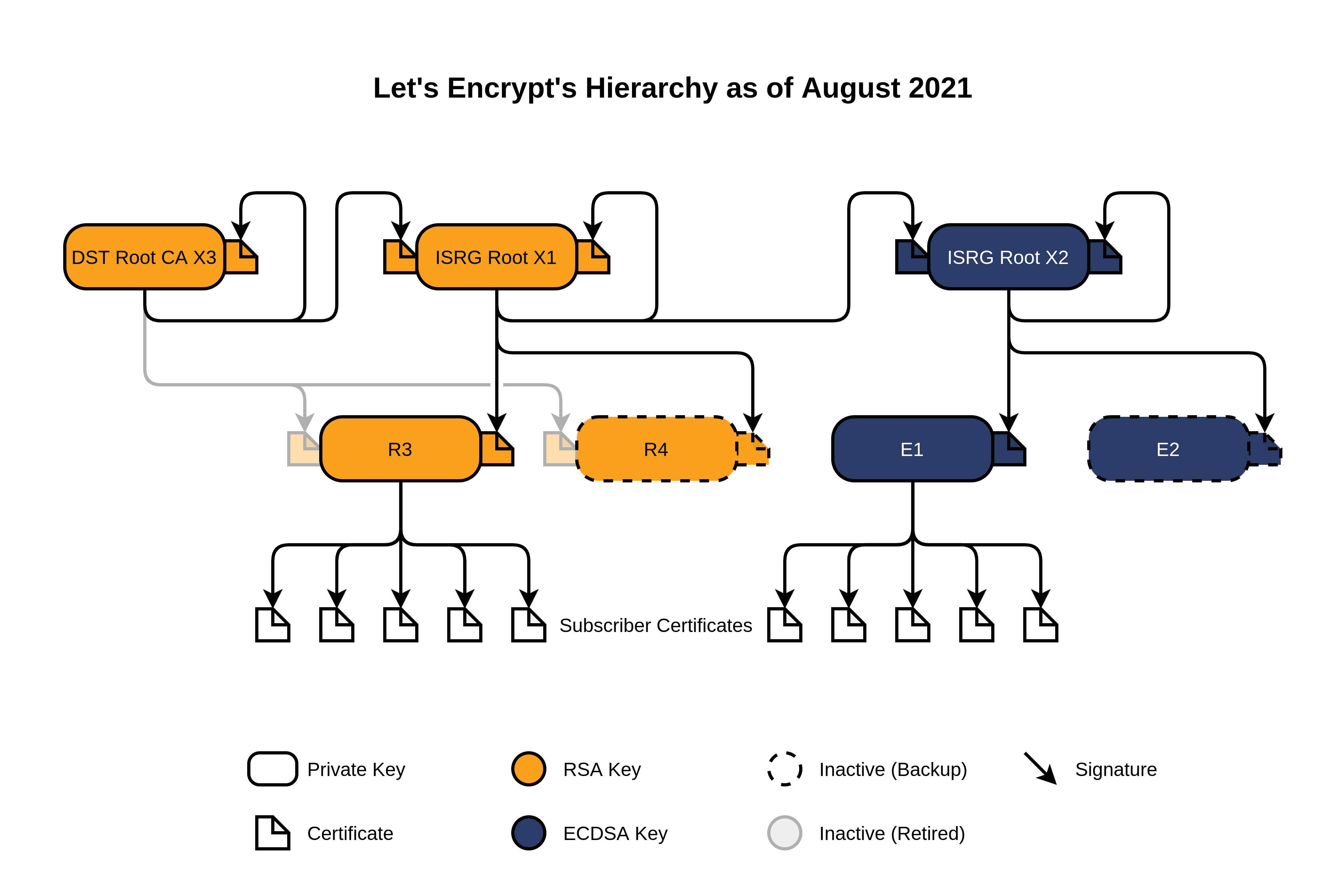
Our roots are kept safely offline. We issue end-entity certificates to subscribers from the intermediates in the next section. For additional compatibility as we submit our new Root X2 to various root programs, we have also cross-signed it from Root X1.
- Active
- ISRG Root X1 (
RSA 4096, O = Internet Security Research Group, CN = ISRG Root X1)
- ISRG Root X1 (
- Active, limited availability
- ISRG Root X2 (
ECDSA P-384, O = Internet Security Research Group, CN = ISRG Root X2)
- ISRG Root X2 (
We’ve set up websites to test certificates chaining to our active roots.
Intermediate Certificates
Under normal circumstances, certificates issued by Let’s Encrypt will come from “R3”, an RSA intermediate. Currently, issuance from “E1”, an ECDSA intermediate, is possible only for ECDSA subscriber keys for allowlisted accounts. In the future, issuance from “E1” will be available for everyone.
Our other intermediates (“R4” and “E2”) are reserved for disaster recovery and will only be used should we lose the ability to issue with our primary intermediates. We do not use the X1, X2, X3, and X4 intermediates anymore.
IdenTrust has cross-signed our RSA intermediates for additional compatibility.
- Active
- Let’s Encrypt R3 (
RSA 2048, O = Let's Encrypt, CN = R3)- Signed by ISRG Root X1: der, pem, txt
- Cross-signed by IdenTrust: der, pem, txt (Retired)
- Let’s Encrypt R3 (
- Active, limited availability
- Let’s Encrypt E1 (
ECDSA P-384, O = Let's Encrypt, CN = E1)
- Let’s Encrypt E1 (
- Backup
- Let’s Encrypt R4 (
RSA 2048, O = Let's Encrypt, CN = R4)- Signed by ISRG Root X1: der, pem, txt
- Cross-signed by IdenTrust: der, pem, txt (Retired)
- Let’s Encrypt E2 (
ECDSA P-384, O = Let's Encrypt, CN = E2)
- Let’s Encrypt R4 (
- Retired
- Let’s Encrypt Authority X1 (
RSA 2048, O = Let's Encrypt, CN = Let's Encrypt Authority X1) - Let’s Encrypt Authority X2 (
RSA 2048, O = Let's Encrypt, CN = Let's Encrypt Authority X2) - Let’s Encrypt Authority X3 (
RSA 2048, O = Let's Encrypt, CN = Let's Encrypt Authority X3) - Let’s Encrypt Authority X4 (
RSA 2048, O = Let's Encrypt, CN = Let's Encrypt Authority X4)
- Let’s Encrypt Authority X1 (
Cross Signing
Intermediates
Each of our intermediates represents a single public/private key pair. The private key of that pair generates the signature for all end-entity certificates (also known as leaf certificates), i.e. the certificates we issue for use on your server.
Our RSA intermediates are signed by ISRG Root X1. ISRG Root X1 is widely trusted at this point, but our RSA intermediates are still cross-signed by IdenTrust’s “DST Root CA X3” (now called “TrustID X3 Root”) for additional client compatibility. The IdenTrust root has been around longer and thus has better compatibility with older devices and operating systems (e.g. Windows XP, Android 7). You can download “TrustID X3 Root” from IdenTrust (or, alternatively, you can download a copy from us).
Having cross-signatures means that each of our RSA intermediates has two certificates representing the same signing key. One is signed by DST Root CA X3 and the other is signed by ISRG Root X1. The easiest way to distinguish the two is by looking at their Issuer field.
When configuring a web server, the server operator configures not only the end-entity certificate, but also a list of intermediates to help browsers verify that the end-entity certificate has a trust chain leading to a trusted root certificate. Almost all server operators will choose to serve a chain including the intermediate certificate with Subject “R3” and Issuer “ISRG Root X1”. The recommended Let’s Encrypt client software, Certbot, will make this configuration seamlessly.
Roots
Similar to intermediates, root certificates can be cross-signed, often to increase client compatibility. Our ECDSA root, ISRG Root X2 was generated in fall 2020 and is the root certificate for the ECDSA hierarchy. It is represented by two certificates: one that is self-signed and one that is signed by ISRG Root X1.
All certificates signed by the ECDSA intermediate “E1” will come with a chain including an intermediate certificate whose Subject is “ISRG Root X2” and whose Issuer is “ISRG Root X1”. Almost all server operators will choose to serve this chain as it offers the most compatibility until ISRG Root X2 is widely trusted.
OCSP Signing Certificate
This certificate is used to sign OCSP responses for the Let’s Encrypt Authority intermediates, so that we don’t need to bring the root key online in order to sign those responses. A copy of this certificate is included automatically in those OCSP responses, so Subscribers don’t need to do anything with it. It is included here for informational purposes only.
- ISRG Root OCSP X1 (Signed by ISRG Root X1): der, pem, txt
Our newer intermediates do not have OCSP URLs (their revocation information is instead served via CRL), so we have not issued an OCSP Signing Cert from ISRG Root X2.
Certificate Transparency
We are dedicated to transparency in our operations and in the certificates we issue. We submit all certificates to Certificate Transparency logs as we issue them. You can view all issued Let’s Encrypt certificates via these links: